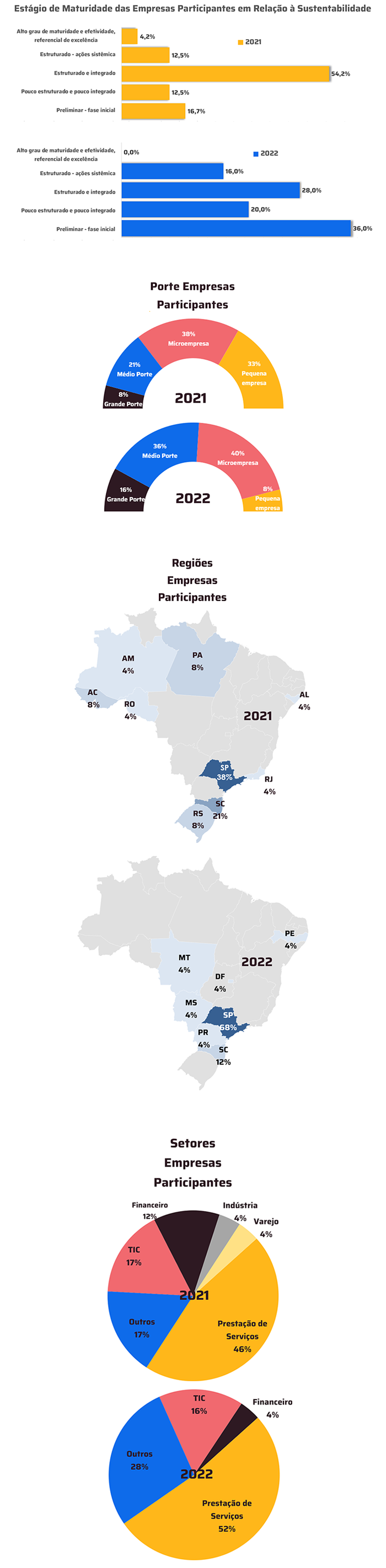
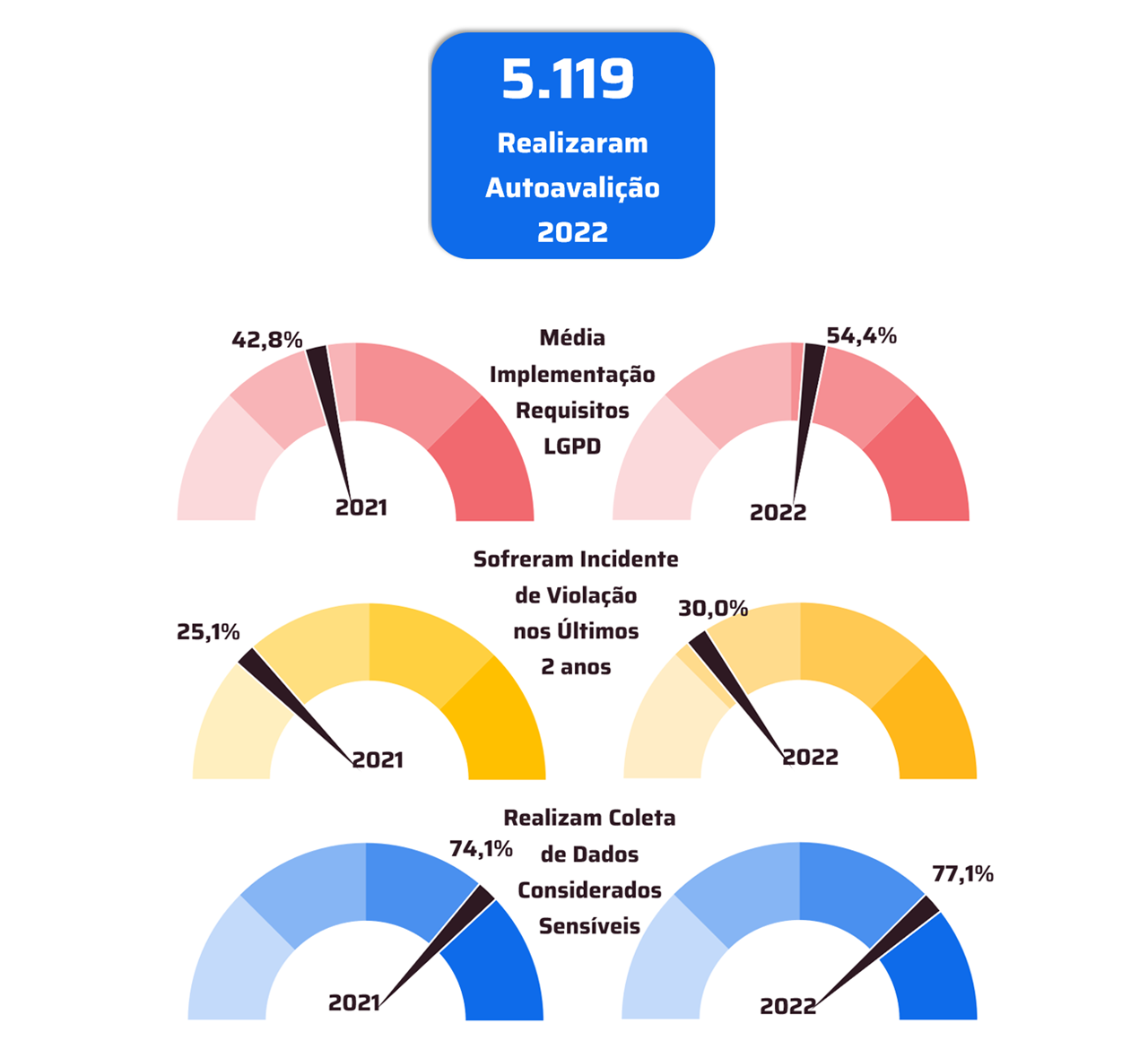
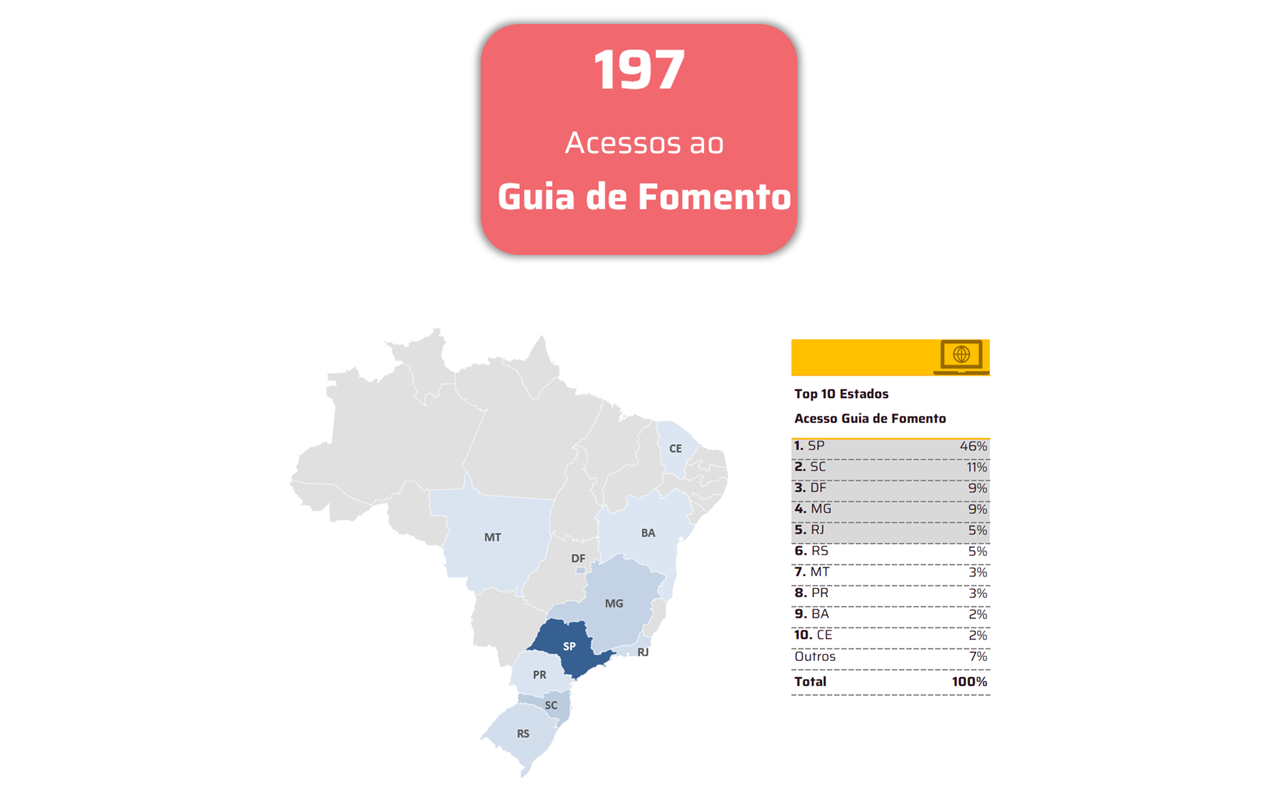
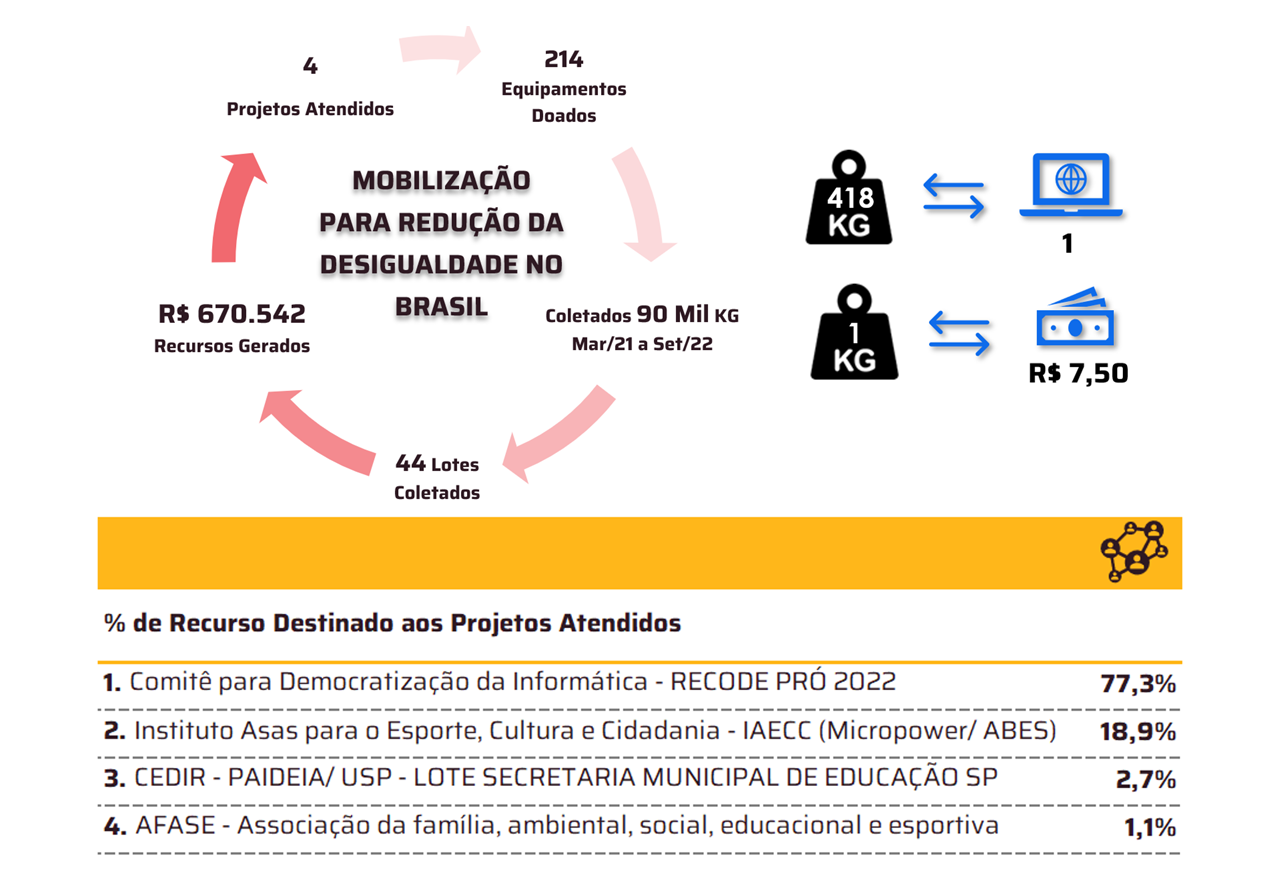
*Per Nivancir Naville
*Per Nivancir Naville
In the digital age, the main threat to any business is no longer the highly sophisticated hacker capable of breaching firewalls, but the attacker who simply logs in using legitimate credentials. With artificial intelligence (AI)-powered phishing, deepfakes, social engineering, and industrial-scale impersonation (the massive and systematic use of advanced techniques to impersonate another person or entity), the entry point to organizations is directly linked to how people access systems. This access has become the most vulnerable point: the human factor.
Cybersecurity still suffers from the confusion between identification and authentication. In 1988, internet architect Dr. David Clark emphasized the need to keep these concepts separate. However, the foundations for today's vulnerabilities were already laid in the 1960s, when password security began to merge identification and authentication. Technological advances in access management, rather than solving the problem, have only deepened the confusion.
Traditional solutions, such as IAM (Identity and Access Management), PAM (Privileged Access Management), and SSO (Single Sign-On), focus on identity verification but often fail to adequately validate or restrict access rights. This gap between identification and authentication opens the door for exploitation by the vast majority of modern attacks.
Human behavior exacerbates the problem: according to a recent survey, approximately 781,000 users still reuse passwords across multiple systems, combining personal and professional access. This means that a single breach can compromise multiple areas and multiply the risk of targeted attacks and network infiltration.
Recent Cases: Attacks in 2025 Expose Credential Fragility
· In April 2025, the Marks & Spencer, a UK retail giant, suffered a massive cyberattack. Hackers exploited stolen credentials to access sensitive customer data, forcing the company to suspend online orders and causing estimated losses of approximately US$1,400 million, in addition to significant damage to the brand's reputation and trust.
· One of the largest data brokers in the US, LexisNexis Risk Solutions, revealed in May 2025 that hackers accessed personal information of more than 364,000 people after a breach of internal systems.
· In Brazil, the technology company Sinqia, essential for financial operations and integration with Pix, revealed that in September it suffered an attack based on the exploitation of legitimate vendor credentials, allowing more than R$700 million to be diverted from the system. The incident profoundly impacted banks and fintechs, in addition to undermining some of the trust in Brazilian instant transaction systems.globe+1
These cases illustrate a trend: more than 90% of breaches in 2025 originate from credential theft or phishing scams, not technical exploits of systems — the weakest link is the human, in a scenario where AI generates hyper-personalized attacks, imitates voices and communication styles, and creates campaigns virtually indistinguishable from legitimate ones.
Strategic shift: from “phishable” to “unphishable”
At MyCena®, we understand that intensifying training or alerts isn't enough. A structural change is needed: making the company unassailable by design.
Nivancir Naville – Country Manager – MyCena Security Solutions
Notice: The opinion presented in this article is the responsibility of its author and not of ABES - Brazilian Association of Software Companies