*Cesar Candido
*Cesar Candido
With the pandemic almost under control, organizations around the world have already returned to the office and many have permanently adopted hybrid work, which includes several days of home office. While each arrangement carries its set of pros and cons, from a cybersecurity perspective there are some challenges that need to be addressed to cover all security gaps.
This hybrid arrangement of work blurs the divide between corporate and home networks, while expanding the attack surface in both environments. So, how to deal with these security breaches?
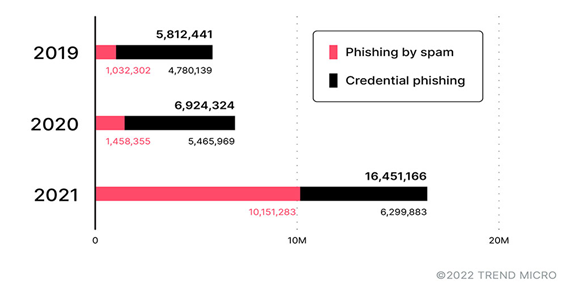
First, we must examine the data to see which threats thrived during the transition period. In 2021, most organizations have settled into remote settings. In our annual summary for that year, we noted that there was a 382% increase in malicious files blocked. Cybercriminals also seem to have doubled down on scams. phishing during the period.
Based on data from Trend Micro™ Cloud App Security, the phishing had an absurd growth of 596%. In the age when the workplace has largely shifted from offices to homes, malicious actors have taken full advantage of email to spread malware as it is a low-effort, high-impact attack vector.
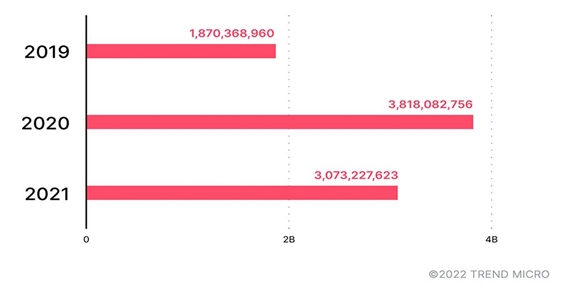
And the home network? Data from the “Smart Home Network” solution showed an increase in potential malicious activity on home networks from 2019 to 2020. The number of threats blocked indicates that home devices, particularly routers, were frequent targets during the period. While this was to be expected, as most employees who stayed at home relied on devices to stay connected and continue their activities, the growth in attacks more than doubled, causing immense concern for the information security industry.
For hybrid working to work, employees need access to company files from their remote locations. However, moving files can increase the likelihood of a data breach or the introduction of malicious files into a company's network. According to research conducted by OpenText - a Canadian company that develops and sells software for managing business information - 56% of US employees use personal file sharing tools in their day-to-day work.
Among the respondents, 76% admitted that they feel stressed by the flood of Home Office context information, while 26% stated that they use 11 or more accounts, features, tools and apps, every day – an overwhelming estimate, to say the least. Minimum.
Organizations must provide their employees with secure ways to transfer large files and access data hosting services. They should also educate employees on what types of files are safe to share and the correct permissions to apply when sharing files.
Virtual Private Networks (VPNs) allowed users to connect to secure networks while working from home. Unfortunately, unsecured vulnerabilities in VPNs have also been exploited in attacks. One of the most used vulnerabilities was CVE-2018-13379. To date, it is the most exploited vulnerability in VPN products, although a patch for it has been available since May 2019. Other vulnerabilities that have seen many exploits include CVE-2019-11510 and CVE-2019-19781.
Enterprises and users alike must be aware of these threats, as hybrid configurations make it easier for them to traverse both home and office networks. As Home Office and hybrid work test the idea of cybersecurity as a shared responsibility, employees and organizations must do everything in their power to prevent threats and bridge the security gap between home and office networks.
Below are some tips for employees:
- Isolate your work devices on your home network;
- Use VPNs to make the connection between your home and office network more secure;
- Configure the security of the routers to limit the possibilities of invasion by cybercriminals; if possible, use a network security tool to get an additional layer of protection for your entire home environment and connected devices;
- Follow your company's rules of good safety practices;
- Be aware of the tactics of phishing and other scams, especially when working in a less secure environment;
- Use only tools, applications, services and accounts made available by the company, avoiding the use and download of unapproved alternatives;
- Always opt for two-factor authentication (2FA) instead of just using simple passwords.
Companies must:
- Control employee access to the VPN and require them to renew their login daily;
- Establish guest networking for use by guests and on personal devices;
- Promote staff training on best digital security practices, in addition to creating a communication line to report suspicious incidents, particularly those with signs of phishing;
- Define tools and establish cloud services for communication between employees and file access and sharing
*Cesar Candido is CEO of Trend Micro in Brazil, a company specialized in cybersecurity
Notice: The opinion presented in this article is the responsibility of its author and not of ABES - Brazilian Association of Software Companies