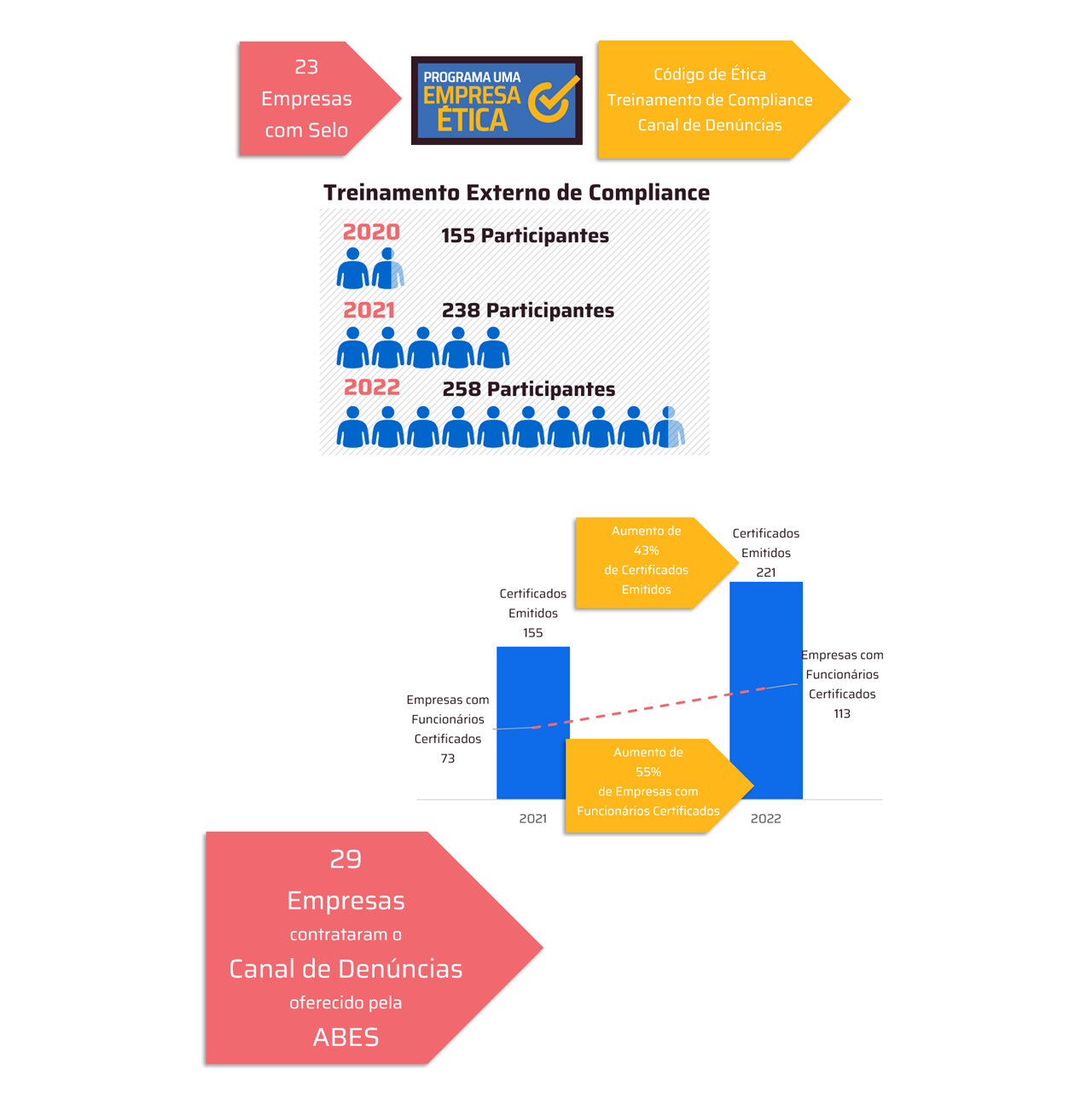
New groups and families of malware require agility in response and highlight the need to simulate violations in protection systems
In another hectic month for CISOS, the report by Picus Security, a pioneer in Breach and Attack Simulation (BAS – Breach and Attack Simulation), shows the emergence of cyberattack campaigns triggered by new groups of hackers and malware families. Among the most significant are: Maui Ransomware, which uses a hybrid encryption method involving AES, RSA encryption and XOR encoding which increases its impact; Green Stone Malware Dropper, which sends Open XML documents containing a malicious macro, which unpacks and runs an executable, with spy features, in a temporary directory, which avoids detection by most antiviruses.
O HavanaCrypt Ransomware was another one that appeared in July. It masquerades as a legitimate Google Software application and uses an IP address belonging to a Microsoft hosting service as its C2 server to avoid detection. Another attack was that of a Ransomware that uses the double extortion method: it steals confidential data, encrypts it and releases a ransom note with a chat address on the Tor Browser, the most used to access the DeepWeb (and therefore , the DarkWeb). already the H0lyGh0st Ransomware, although it has been active since 2021, the group now strikes back with a more persistent and improved variant of this malware, BTLC.exe.
“Without cyber resilience, companies, government entities and other organizations are doomed to become the next victims of ransomware and countless other cyberattacks, as we have seen around the world”, warns Tom Camargo, VP of CLM, Latin American distributor value-added focused on information security, data protection, infrastructure for data centers and cloud.
For the CLM executive, which distributes Picus technology in Latin America, in this extremely dynamic scenario and marked by the emergence of new groups of cybercriminals, acting with new forms of attack, the agility in the response proves to be increasingly essential to avoid the data hijacking and other evils caused by a growing number of cyber threats. “The support of technologies that quickly simulate danger makes it possible to test the effectiveness of security controls. O Picus Labs included simulations of the various attacks registered in July in the Picus Threat Library, updating the Picus Complete Security Control Validation platform in real time”.
See details of the top five attacks in this period below:
1. Maui Ransomware
The Cybersecurity and Infrastructure Security Agency (CISA), the US Treasury Department and the Federal Bureau of Investigation (FBI) released a joint statement on July 6 about a cyber threat actor based in North Korea using , Maui ransomware. Groups affiliated with this ransomware are mostly known for inflicting apparently North Korean government-sponsored ransomware attacks on healthcare sectors. Maui employs a single extortion method, so it does not exfiltrate data or remove system backups.
The curious thing is that it does not employ a lateral movement technique (when the attacker spreads from a non-confidential point or account to the rest of the network) and does not send a note instructing its victims to pay the ransom. However, Maui uses a hybrid encryption method combining AES, RSA encryption, and XOR encryption for increased impact. While the RSA algorithm generates a new public-private key pair, the AES algorithm encrypts each file in CBC mode. After each file is encrypted with a unique secret key, those secret keys are encrypted with the public key that is generated right at the start of the attack.
The Picus Threat Library included the following threats for Maui ransomware: Maui Ransomware Download Threat (Network Infiltration) – ID 56700 and Maui Ransomware Email Threat (Email Infiltration (Phishing)) – ID 64940
2. Green Stone Malware Dropper
In late July, many Iranian companies received an Office Open XML document containing a malicious macro, whose functions unpack and run an executable in a temporary directory, which is a common practice employed in cyberattacks to avoid detection. Further analysis showed that the executable has cyber-espionage capabilities. It collects information about the operating system, takes screenshots and sends the collected data to a remote server.
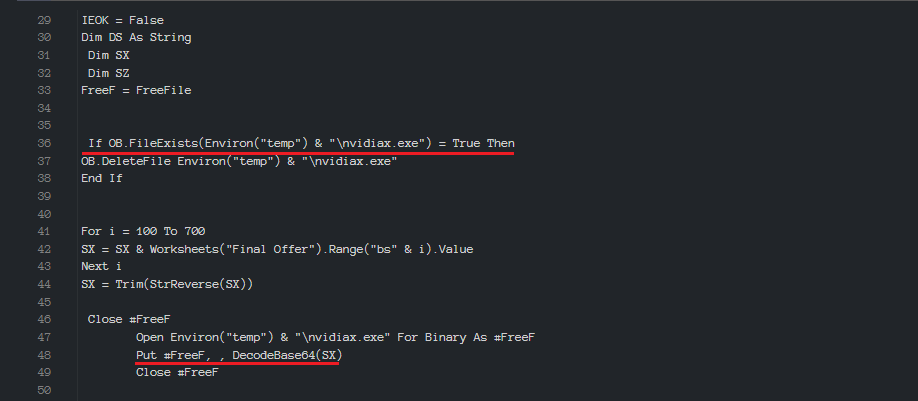
Figure 1: Malicious executable contained in the Office Open XML document: Green Stone Malware Dropper
Analysis of this malware points to an unusual technique of exchanging commands using a Telegram bot. This technique avoids unnecessary communications with a remote server and hides the C2 server.
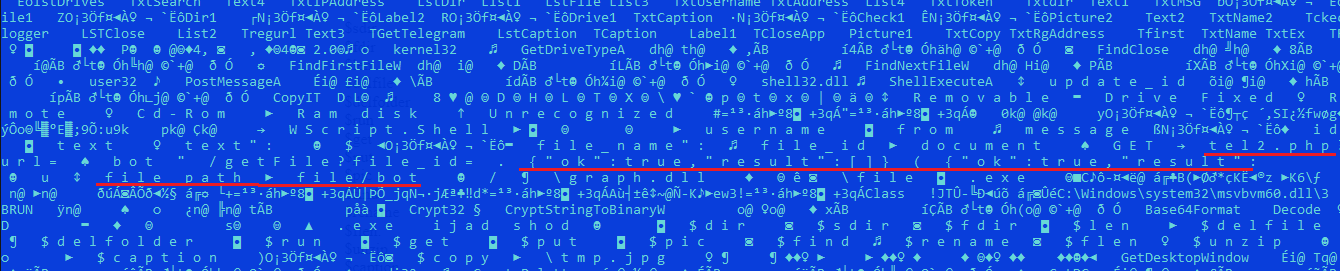 Figure 2: Commands supported via a Telegram bot
Figure 2: Commands supported via a Telegram bot
“As many groups that use APT (advanced persistent threat) prefer to embed malicious content in a document that seems harmless, companies need to be aware of the possible threats coming from emails and evaluate the effectiveness of their XDR protection against Spam, Phishing and various malware , like the Green Stone Malware Dropper”, recommends Camargo.
The Picus Threat Library includes the following threats for the Green Stone malware dropper: Green Stone Malware Dropper Email Threat (Email Infiltration (Phishing)) – ID 69096 and Green Stone Malware Dropper Download Threat (Network Infiltration) – ID 70452
3. The HavanaCrypt Ransomware
The year 2022 was marked by the distribution of malware disguised as legitimate programs and software updates, such as Windows 10, Google Chrome and Microsoft Exchange. This month, a new malware family, HavanaCrypt, was found in native state. This malware masquerades as a legitimate Google Software application and uses an IP address belonging to a hosting service on Microsoft Azure, which is the C2 server, to appear legitimate. Further analysis showed that the malware uses the QueueUserWorkItem function to implement a threat array for its other payloads and a .NET System.Threading namespace method, which allows a sequence of execution methods. HavanaCrypt uses KeePass Password Safe modules, an open source password manager, during the file encryption process.
This malware is an application compiled in .NET and protects its code in a .NET assembly using Obfuscate, an open source .NET obfuscator.
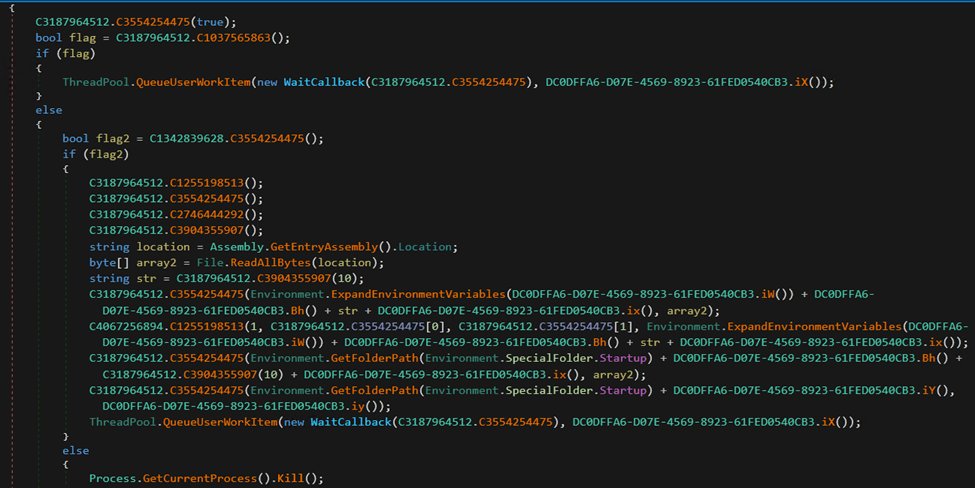
Figure 3. Obfuscated sample of HavanaCrypt
HavanaCrypt malware is designed to have several anti-virtualization techniques to avoid dynamic analysis in case it runs in a virtual machine. It even scans services mostly used by virtual machines like VMware Tools, VMTools and mouse wm???????? To analyze this malware, researchers used deobfuscation tools such as DeObfuscar and de4dot.
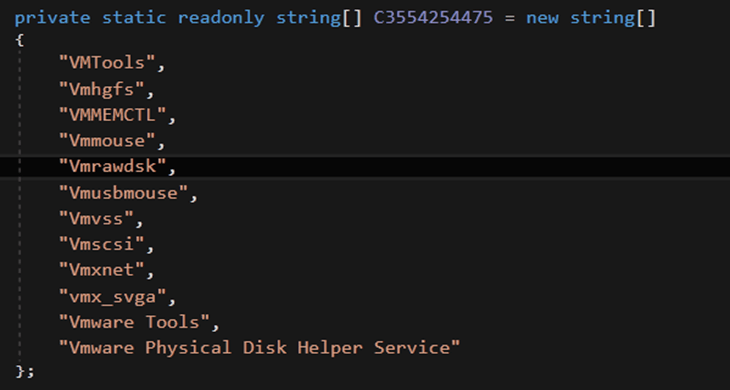
Figure 4. Services scanned by HavanaCrypt malware
Browser Tor directories have been found to be among the targets that HavanaCrypt avoids encrypting. The attackers may have planned to communicate with their victims via the Tor browser. Another strange thing that stands out is that criminals do not send ransom notes. “With that in mind, the researchers think that HavanaCrypt is still in the development process. However, it is important that organizations test their system against this new family of malware”, warns the CEO of CLM.
The Picus Threat Library includes the following threats for HavanaCrypt: HavanaCrypt Ransomware Email Threat (Email Infiltration (Phishing)) – ID 24728 and HavanaCrypt Ransomware Download Threat (Network Infiltration) – ID 91290
4. Lilith Ransomware
A C/C++ console-based ransomware called Lilith has been discovered in its native state. This malware is designed for the Windows x64 architecture, and like many other ransomware operations, Lilith uses the double extortion method: it steals sensitive data, encrypts it, and sends a ransom note by providing a chat address in the Tor browser. on the target system.
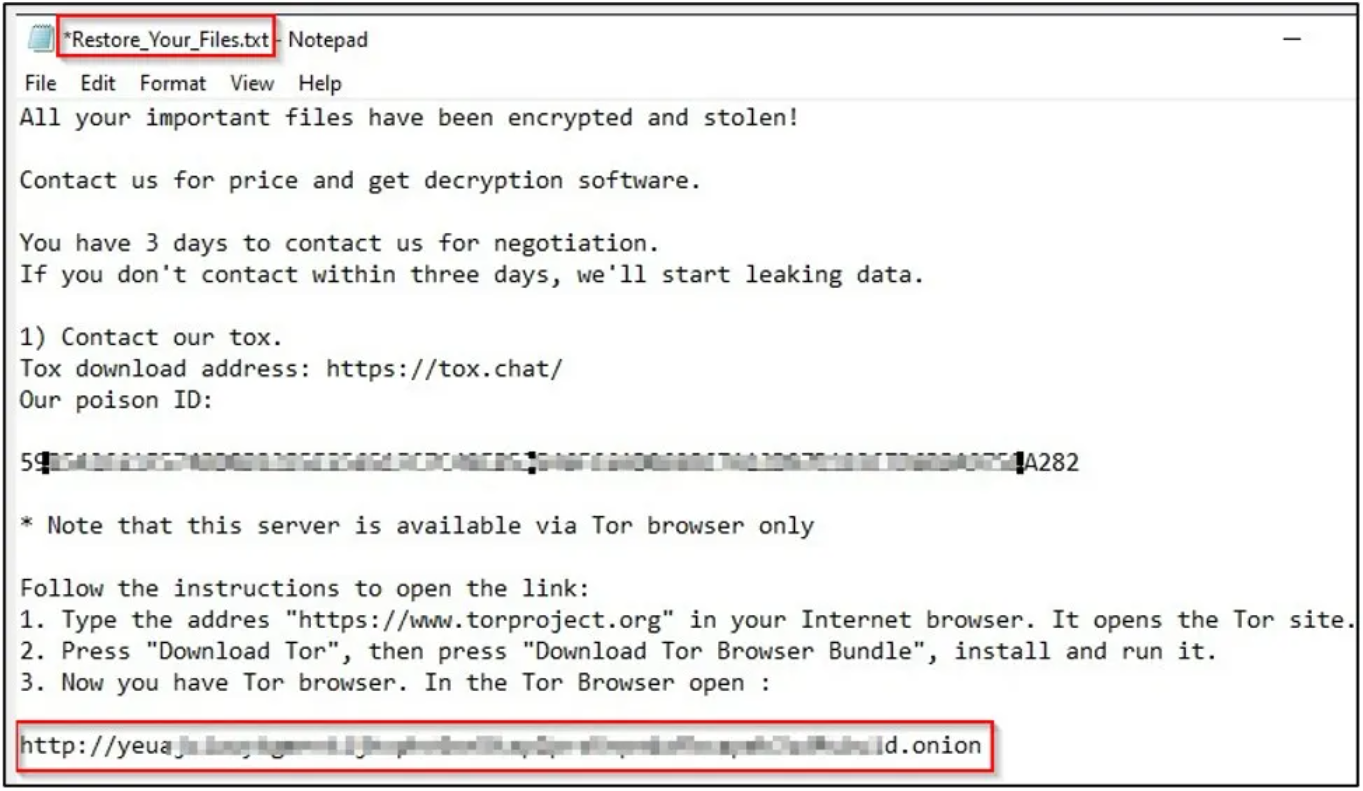
Figure 5: Ransom note sent by attackers
Analysis shows that Lilith malware does not encrypt all types of files on the target System. For example, EXE, DLL, SYS and Program Files, Web browsers and Trash Folders are excluded from the encryption process. In addition to these files, a strange file found on the victim's system stands out: ecdh_pub_k.bin. This file is also excluded from the encryption process and stores the local public key of the BABUK ransomware infections, indicating that these two malware families may be linked in some way.
The malware performs encryption using a Windows cryptographic API and the Windows CryptGenRandom function to generate a random key. While the researchers say the new Lilith family is nothing new, it is one of the latest that organizations need to test their systems.
The Picus Threat Library includes the following threats for Lilith ransomware: Lilith Ransomware Email Threat (Email Infiltration (Phishing)) Lilith Ransomware Download Threat (Network Infiltration) – ID 35395 and Lilith Ransomware Download Threat (Network Infiltration) – ID 94407
5. H0lyGh0st Ransomware
H0lyGh0st is a North Korean cyber extortion threat group known for developing malware payloads and perpetrating ransomware attacks since June 2021. In 2018, they launched many successful attacks against small and medium-sized businesses such as banks , manufacturers, schools and event and meeting planning companies worldwide.
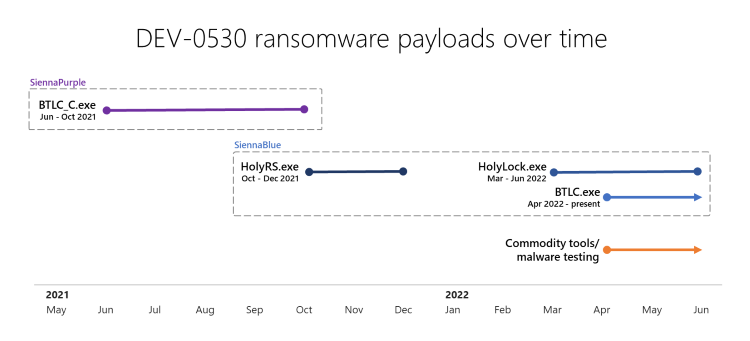
Figure 6: Timeline of payloads developed and used by H0lyGh0st
Although H0lyGh0st has been around since 2021 and tracked by MSTIC (Microsoft Threat Intelligence Center) at the time, the group now strikes back with a more persistent and improved malware variant: BTLC.exe.
The Picus Threat Library includes the following threats for H0lyGh0st ransomware: H0lyGh0st Ransomware Malware Download Threat (Network Infiltration) – ID 20076; H0lyGh0st Ransomware Malware Email Threat (Email Infiltration (Phishing)) – ID 41450; DEV-0530 Threat Group Campaign Malware Download Threat (Network Infiltration) – ID 97451 and DEV-0530 Threat Group Campaign Malware Email Threat (Email Infiltration (Phishing)) – ID 75946
About CLM
CLM is a value-added Latin American distributor focused on information security, data protection, data center infrastructure and cloud. The company recently received three awards: the best distributor in Latin America by Nutanix, an award won for the quality and agility in the services provided to the channels; the Lenovo/Intel Best Growth LA Partner award given to the company that stands out the most in terms of sales growth; and the Infor Channel Distribution Excellence, an achievement that is due to CLM's commitment to excellence and tireless pursuit of providing the best solutions and services to business partners.
Headquartered in São Paulo, the company has affiliates in the US, Colombia, Peru and Chile. With an extensive network of VARs in Latin America and enormous experience in the market, CLM is constantly looking for innovative and disruptive solutions to provide more and more value for its channels and customers. www.CLM.international
About Picus Security
Founded in 2013 by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security pioneered Breach and Attack Simulation (BAS) technology, helping organizations improve their cyber resilience ever since. The company is recognized by Frost & Sullivan as one of the most innovative vendors in the BAX market, as well as being the highest rated BAS company by Gartner Peer Insights. www.PicusSecurity.com